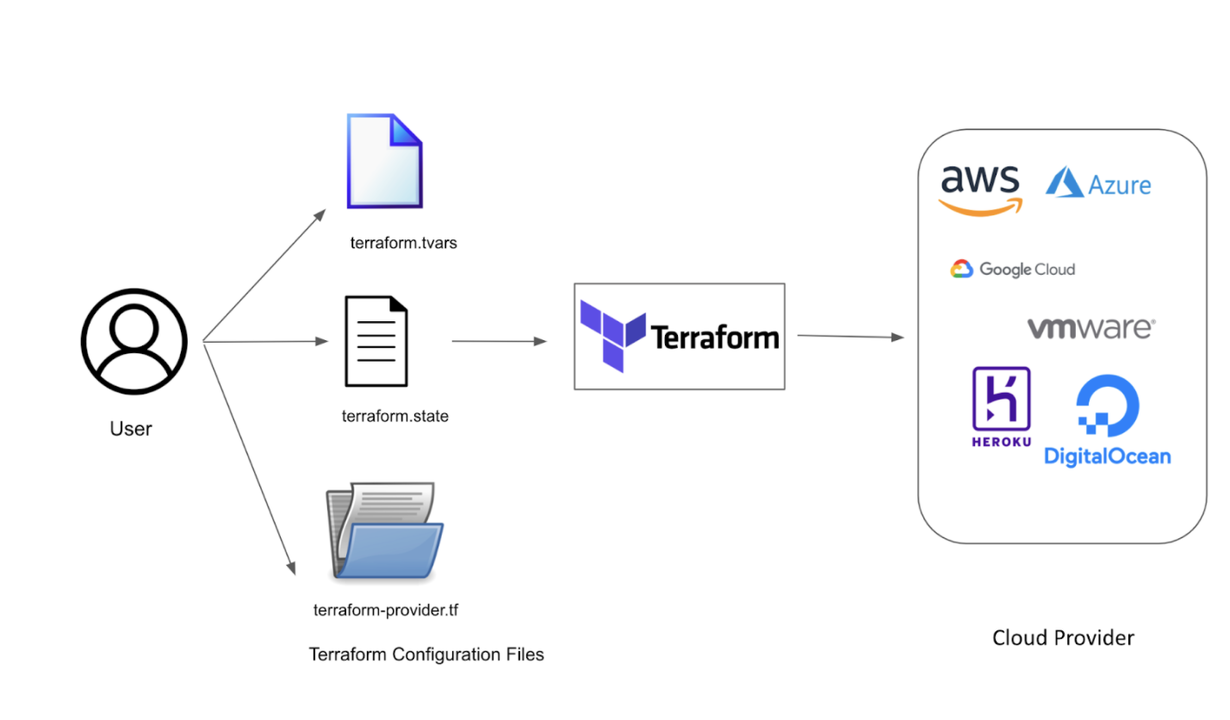
This script automates the setup of a basic infrastructure in Azure, including networking components like virtual networks, subnets, and security groups, as well as deploying a virtual machine with a public IP address and custom startup tasks.
# Set the Azure Provider source and version being used
terraform {
required_version = ">= 0.14"
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = "~> 3.1.0"
}
}
}
# Configure the Microsoft Azure provider
provider "azurerm" {
features {}
}
# Create a Resource Group if it doesn’t exist
resource "azurerm_resource_group" "main" {
name = "my-terraform-rg"
location = "eastus"
}
# Create a Virtual Network
resource "azurerm_virtual_network" "main" {
name = "my-terraform-vnet"
location = azurerm_resource_group.main.location
resource_group_name = azurerm_resource_group.main.name
address_space = ["10.0.0.0/16"]
tags = {
environment = "my-terraform-env"
}
}
# Create a Subnet in the Virtual Network
resource "azurerm_subnet" "main" {
name = "my-terraform-subnet"
resource_group_name = azurerm_resource_group.main.name
virtual_network_name = azurerm_virtual_network.main.name
address_prefixes = ["10.0.2.0/24"]
}
# Create a Public IP
resource "azurerm_public_ip" "main" {
name = "my-terraform-public-ip"
location = azurerm_resource_group.main.location
resource_group_name = azurerm_resource_group.main.name
allocation_method = "Static"
tags = {
environment = "my-terraform-env"
}
}
# Create a Network Security Group and rule
resource "azurerm_network_security_group" "main" {
name = "my-terraform-nsg"
location = azurerm_resource_group.main.location
resource_group_name = azurerm_resource_group.main.name
security_rule {
name = "HTTP"
priority = 1001
direction = "Inbound"
access = "Allow"
protocol = "Tcp"
source_port_range = "*"
destination_port_range = "8080"
source_address_prefix = "*"
destination_address_prefix = "*"
}
tags = {
environment = "my-terraform-env"
}
}
# Create a Network Interface
resource "azurerm_network_interface" "main" {
name = "my-terraform-nic"
location = azurerm_resource_group.main.location
resource_group_name = azurerm_resource_group.main.name
ip_configuration {
name = "my-terraform-nic-ip-config"
subnet_id = azurerm_subnet.main.id
private_ip_address_allocation = "Dynamic"
public_ip_address_id = azurerm_public_ip.main.id
}
tags = {
environment = "my-terraform-env"
}
}
# Create a Network Interface Security Group association
resource "azurerm_network_interface_security_group_association" "main" {
network_interface_id = azurerm_network_interface.main.id
network_security_group_id = azurerm_network_security_group.main.id
}
# Create a Virtual Machine
resource "azurerm_linux_virtual_machine" "main" {
name = "VM01"
location = azurerm_resource_group.main.location
resource_group_name = azurerm_resource_group.main.name
network_interface_ids = [azurerm_network_interface.main.id]
size = "Standard_DS1_v2"
computer_name = "VM01"
admin_username = "azureuser"
admin_password = "ChoosePassword"
disable_password_authentication = false
source_image_reference {
publisher = "Canonical"
offer = "UbuntuServer"
sku = "18.04-LTS"
version = "latest"
}
os_disk {
name = "my-terraform-os-disk"
storage_account_type = "Standard_LRS"
caching = "ReadWrite"
}
tags = {
environment = "my-terraform-env"
}
}
# Configurate to run automated tasks in the VM start-up
resource "azurerm_virtual_machine_extension" "main" {
name = "hostname"
virtual_machine_id = azurerm_linux_virtual_machine.main.id
publisher = "Microsoft.Azure.Extensions"
type = "CustomScript"
type_handler_version = "2.1"
settings = <<SETTINGS
{
"commandToExecute": "echo 'Hello, World' > index.html ; nohup busybox httpd -f -p 8080 &"
}
SETTINGS
tags = {
environment = "my-terraform-env"
}
}
# Data source to access the properties of an existing Azure Public IP Address
data "azurerm_public_ip" "main" {
name = azurerm_public_ip.main.name
resource_group_name = azurerm_linux_virtual_machine.main.resource_group_name
}
# Output variable: Public IP address
output "public_ip" {
value = data.azurerm_public_ip.main.ip_address
}